ENTERPRISE WEB PROXY SERVERS
Fognigma's Portal Proxy Solution
Disguise and Hide Online Resources From Your Adversaries
Hide Online Connections
Portal Proxies obfuscate a user’s true path while connected to online resources, making it very difficult to determine where a user is actually going online.
On-Demand Misdirection
Create a Portal Proxy with just a few clicks in the Fognigma UI. New Web Proxies are ready to use in the time it takes to read this sentence.
Misattribute Users
By using different Portal Proxies, users cannot be identified as originating from, or arriving at, identical Internet locations. They can work together yet appear separate.
Destroy at Any Time
Portal Proxies can be destroyed either manually or scheduled automatically. In fact, admins can turn Portal Proxies on and off at any time – Helpful, for example, if they need to be active only during specific hours.
Disguise Your Internet Activity
& Your Own Websites
Portal Proxies are rapidly generated PaaS instances that disguise the location of important resources and external Fognigma engine interactions. Proxies allow users to visit websites via unique URLs that are different from the actual site URLs, so no trace of where the user actually went is left on the local machine. In addition, the web server never sees the Internet address of the user’s computer.
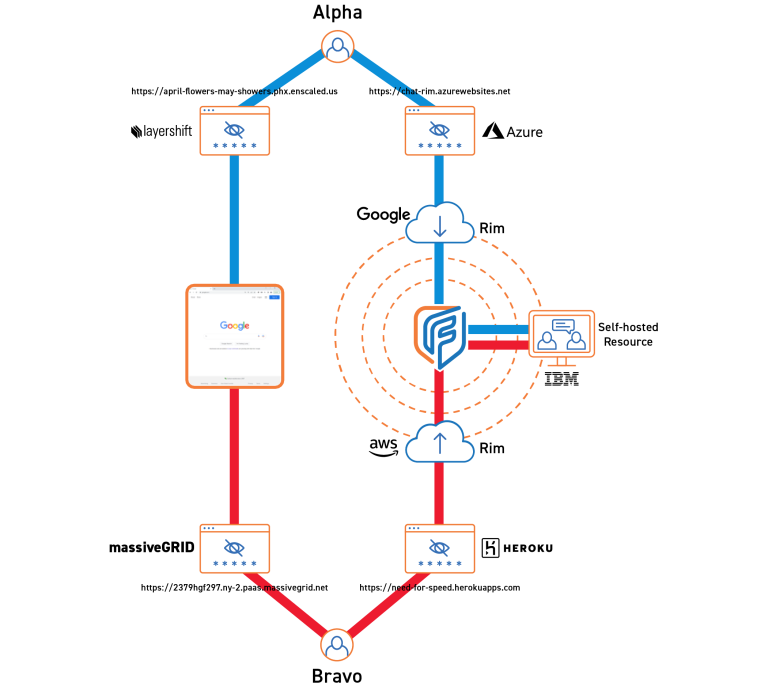
PORTAL PROXIES IN ACTION
Scenario
An organization’s employees are traveling and working remotely in an unsecured location under
surveillance. Due to the nature of the organization’s work, it’s imperative that the employees’ connection to the organization remains hidden to prevent corporate espionage. To avoid compromising the employees, the organization creates Portal Proxies to allow the employees to communicate with the organization’s servers safely.
Using the Fognigma user interface, the organization creates a unique Portal Proxy and a set of credentials for each user.
Users access the Portal Proxy URLs and enter their user credentials.
The users’ devices send a request to the Portal Proxy host provider, which sends a request to the organization’s server and creates a connection, leaving no record of any connection between users and destination.